Compromised credentials remain the leading cause of data breaches globally, according to major threat intelligence reports. Understanding the mechanics of how attackers target your passwords is the first step toward building a robust personal or enterprise security strategy. By demystifying these common attack vectors, we can move from reactive measures to a proactive “prevention-first” mindset.
Method 1: The Art of the Guess
The simplest way into a system is often a direct guess. Attackers don’t just rely on their imagination; they use intelligence. This might involve researching an individual’s personal life or, more commonly, checking for physical “leaks.” Security experts often refer to the “PC Sunflower”—a collection of yellow sticky notes around a laptop screen containing sensitive credentials.
Beyond physical notes, hackers leverage massive databases of previously leaked passwords available on the public internet. Most systems implement a “three strikes” policy to prevent infinite guessing, but an intelligent first or second guess is often all an attacker needs.

Method 2: Harvesting Credentials
In a harvesting attack, the hacker doesn’t guess; they steal the exact password you use. This is primarily done through two methods:
- Malware: “Keyloggers” or “Info-stealers” are installed on a victim’s device to record every keystroke and send it back to the attacker in real-time.
- Phishing: Attackers trick users into visiting a fake website that mimics a legitimate login page. When the user enters their credentials, the data flows directly to the bad actor.
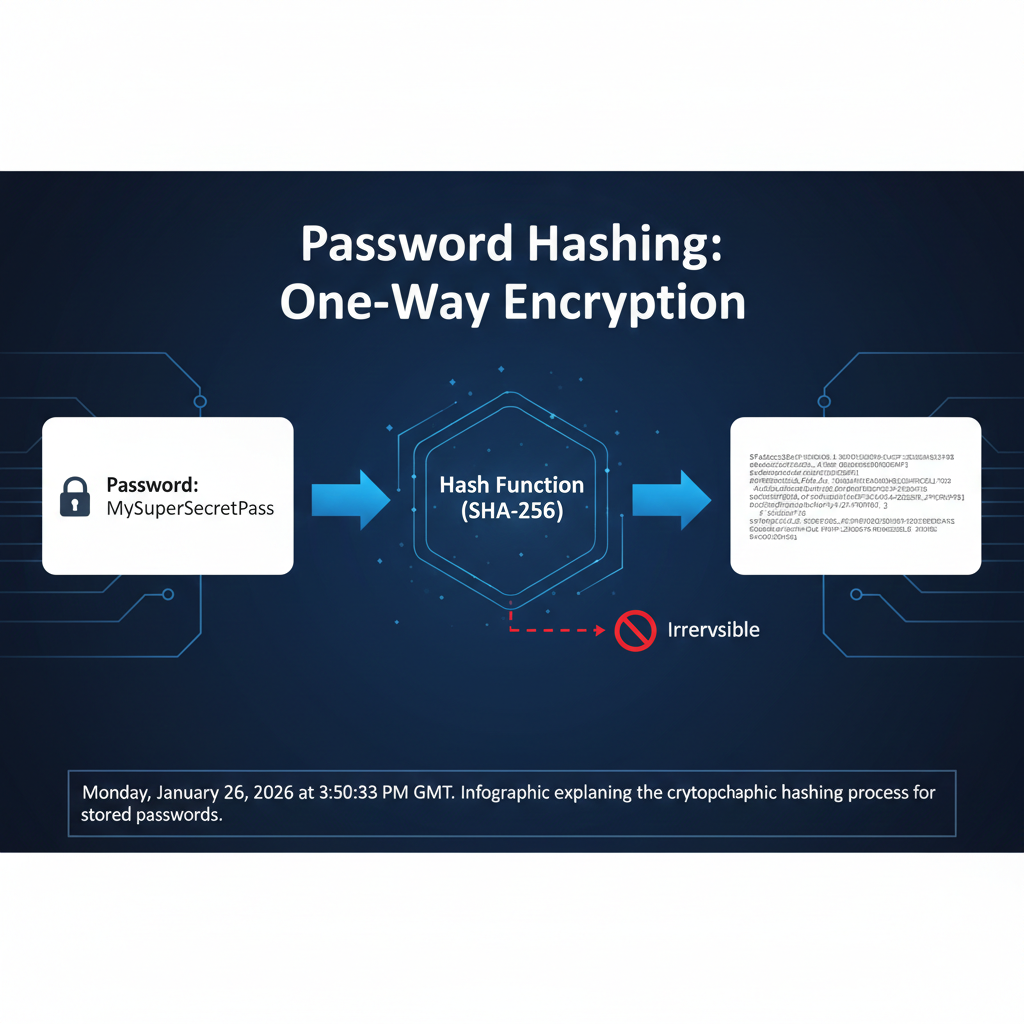
Method 3: Password Cracking (Reversing the Irreversible)
When hackers breach a database, they usually find “hashes” rather than plain text passwords. Hashing is a one-way encryption technique that is mathematically impossible to reverse. However, hackers can “back their way” into discovering the original password.
They do this by taking a list of common passwords (dictionary attacks) or every possible combination (brute force), hashing those guesses, and comparing them to the stolen hashes. If the hashes match, the hacker has found the password without ever actually breaking the encryption.
Method 4 & 5: Spraying and Stuffing
These two techniques exploit the human tendency to reuse passwords across different accounts:
- Password Spraying: An attacker takes one common password and “sprays” it across thousands of different accounts on a single system. This avoids “three strikes” lockouts because they only try the password once per account, flying low under the security radar.
- Credential Stuffing: This is a variation where the attacker takes a known password/username pair from a previous breach and tries it across multiple different systems (e.g., trying your leaked Netflix password on your bank or email accounts).
Defense: Moving Toward a Passwordless Future
To protect yourself, security experts recommend a multi-layered approach involving prevention, detection, and response.
For Prevention:
- Use Password Managers: These tools generate long, unique, and complex passwords for every site, meaning a breach at one service doesn’t compromise your entire digital life.
- Enable Multi-Factor Authentication (MFA): Relying on something you know (a password) is no longer enough. Combine it with something you have (a phone notification) or something you are (biometrics).
- Adopt Passkeys: The gold standard of security is removing the password entirely. Passkeys use advanced cryptography and are significantly harder for attackers to compromise.
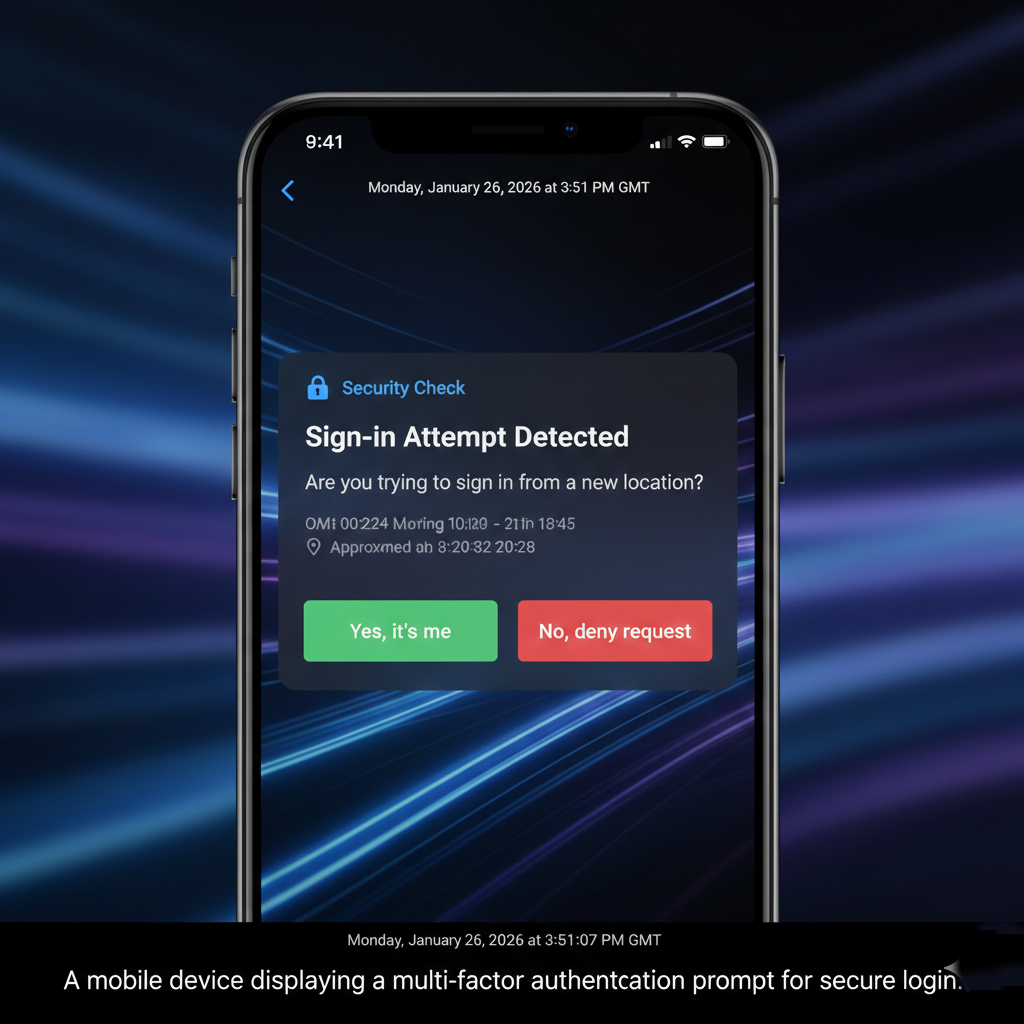
For Detection and Response: Systems should be monitored for unusual bursts of login failures over time or across multiple accounts. If an attack is detected, the immediate response should involve blocking suspicious IP addresses, disabling compromised accounts, and forcing a mandatory password change to render stolen information useless.
















Leave a comment