Introduction: The Tip of the Iceberg
You think you know the internet. You use Google, scroll through social media, and watch YouTube. But what if I told you that you’ve only seen the tip of the iceberg?
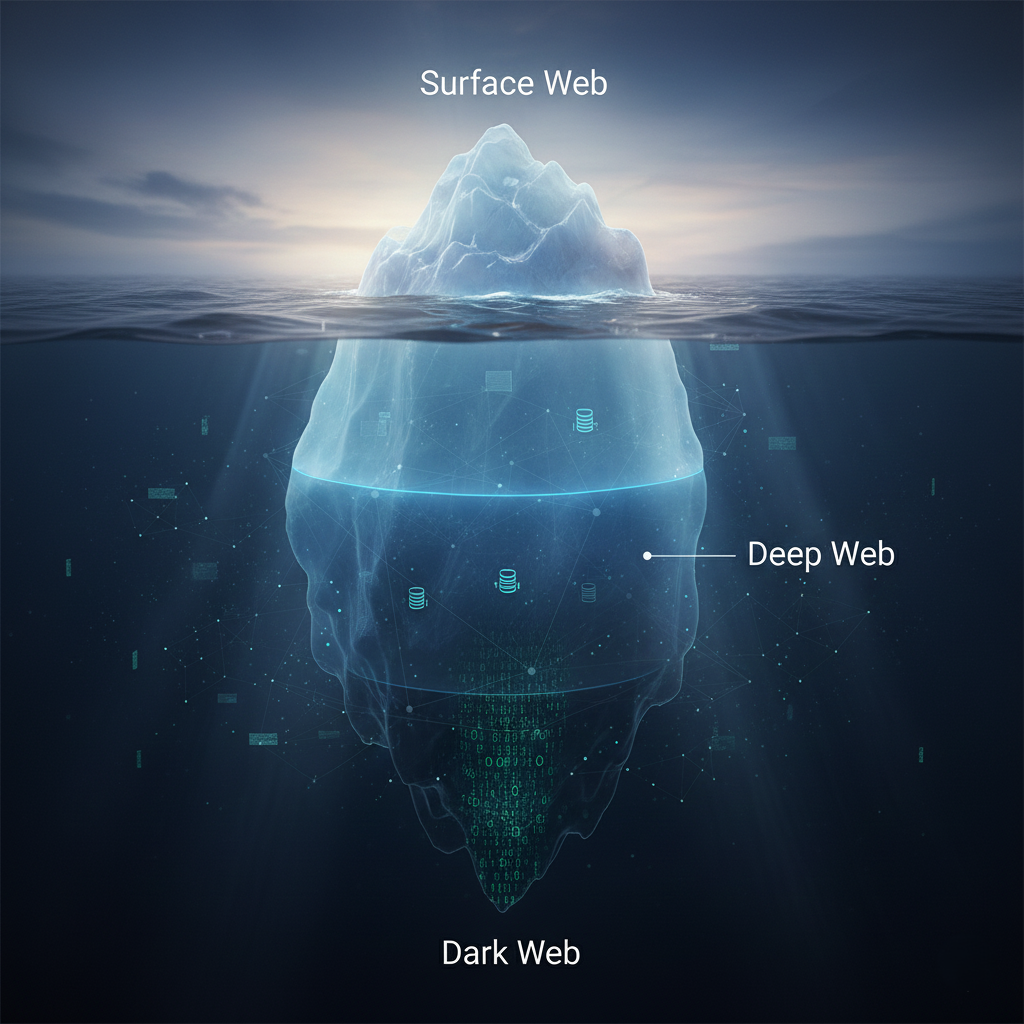
In reality, the “Surface Web”—the part you can find via search engines—makes up only about 5% of the World Wide Web [00:37]. The other 95% is hidden beneath the surface, split into two mysterious layers: the Deep Web and the Dark Web.
What exactly is lurking down there, and is it as dangerous as they say? Let’s dive in.
🌊 The Three Layers of the Web
To understand the Dark Web, we first need to map out the entire internet ecosystem.
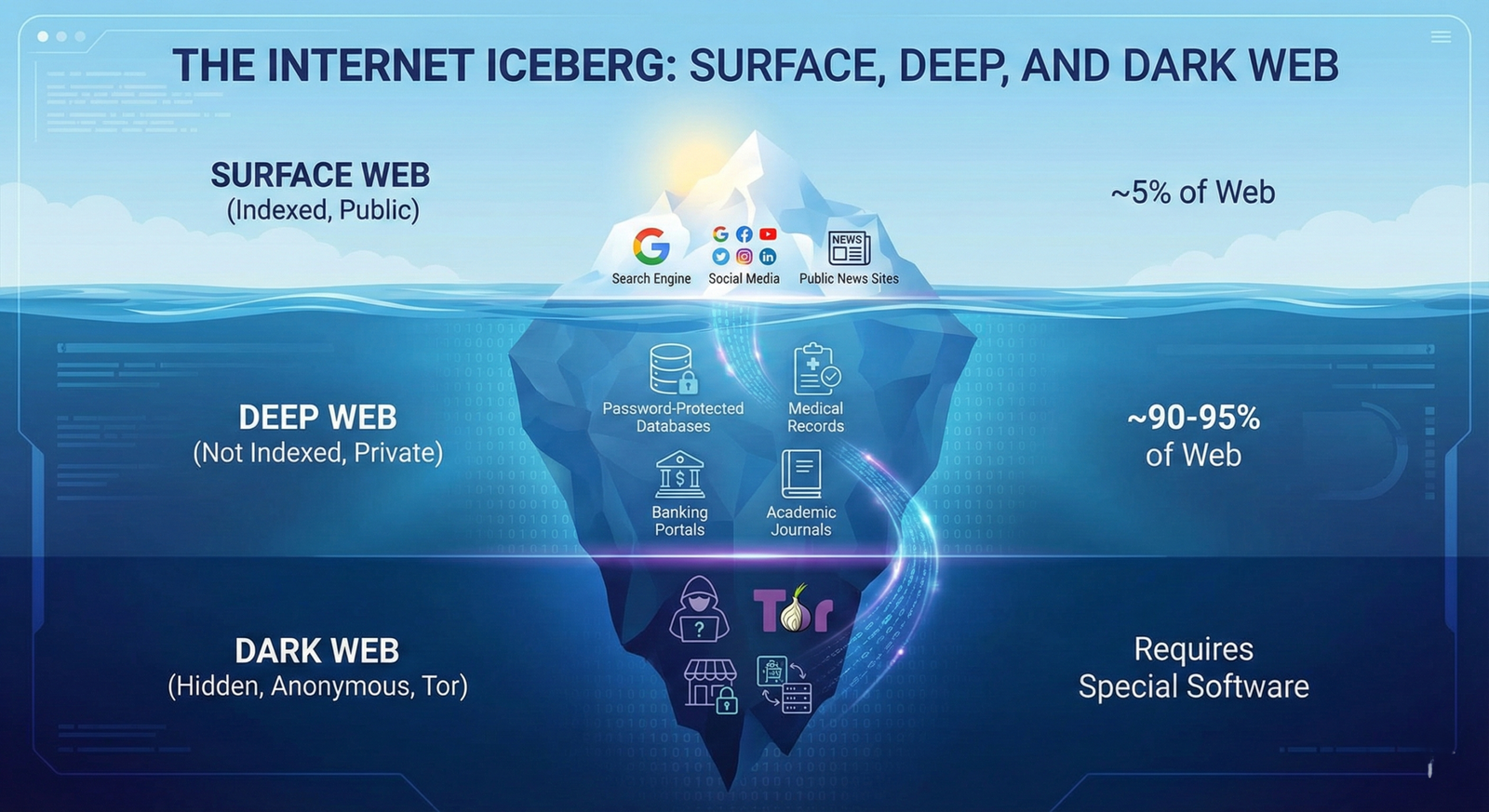
1. The Surface Web (5%)
This is the “indexed” portion of the web. It’s everything you can find on Google, Bing, or Yahoo.
- Examples: Facebook, Instagram, YouTube, News sites, Wikipedia.
- Accessibility: Open to everyone with a browser.
2. The Deep Web (The Majority)
This makes up the vast majority of the internet (part of the non-indexed 95%). Contrary to popular belief, the Deep Web isn’t necessarily nefarious [01:30]. It simply consists of content that isn’t indexed by search engines because it is private or password-protected.
- Examples: Medical records, legal documents, private corporate forums, your online banking dashboard, or subscription-only content.
- Vibe: Boring, administrative, and private.
3. The Dark Web (The Wild West)
This is the deepest part of the internet. It is not indexed, and you cannot access it with a standard browser like Chrome or Safari. It requires specific software to enter, and anonymity is the currency of the realm.

🕵️♂️ What Actually Happens on the Dark Web?
The Dark Web is a dual-use technology. It is a tool for both freedom and crime [02:09].
The Good: Privacy & Freedom
- Whistleblowers: People who need to report sensitive information safely.
- Journalists: Reporters working in oppressive regimes use it to communicate without censorship.
- Political Activists: Citizens in countries without free speech use the Dark Web to organize and share information anonymously [02:42].
The Bad: The Black Market
- Illegal Marketplaces: Sites selling drugs, weapons, and contraband.
- Hacker Forums: A hub for cybercriminals to exchange malware, exploits, and stolen credentials (usernames/passwords) [03:11].
- The Risk: It is a “bad neighborhood.” You are likely to encounter scams, disturbing content, and malware just by browsing.

🧅 How Do You Access It? (The TOR Network)
You can’t just type a Dark Web address into Google. You need The Onion Router (Tor).
How Tor Works
Developed originally by the U.S. Navy and now open-source, Tor is designed to decentralize your traffic to preserve anonymity [04:00].
- Entry Node: Your traffic enters the network (encrypted).
- Middle Nodes: Your traffic bounces through random volunteer computers around the world.
- Exit Node: Your traffic leaves the network to reach the destination site.
Why “Onion”? Because like an onion, your data is wrapped in multiple layers of encryption. Each node only knows the previous and next step, never the full path. No single point knows both who you are and where you are going.
⚠️ The Dangers: Why You Should Probably Stay Away
While Tor provides anonymity, it does not guarantee safety.
- Malware: Sites can automatically download viruses onto your computer.
- Exit Nodes: The final node in the Tor network decrypts your traffic. If you are on an unencrypted site (HTTP), the owner of the exit node can see your data [05:50].
- Speed: Bouncing traffic around the world makes the Dark Web incredibly slow.
Safety Checklist (If You Must Go)
- Use a Sandbox: Run Tor in a isolated environment so malware can’t infect your main system [07:15].
- Use a VPN: Add an extra layer of encryption (Belt and Suspenders approach).
- Don’t Click Random Links: Just like a rough neighborhood, don’t walk down dark alleys you don’t know.

🏁 Conclusion: A Tool, Not a Villain
The Dark Web isn’t inherently evil; it is just a technology that offers extreme privacy. While criminals abuse it, it remains a vital lifeline for activists and journalists living under oppression.
For the average user, however, the risks outweigh the rewards. Unless you have a specific, legitimate reason to be there, it’s best to stay on the surface where the sun shines.














Leave a comment